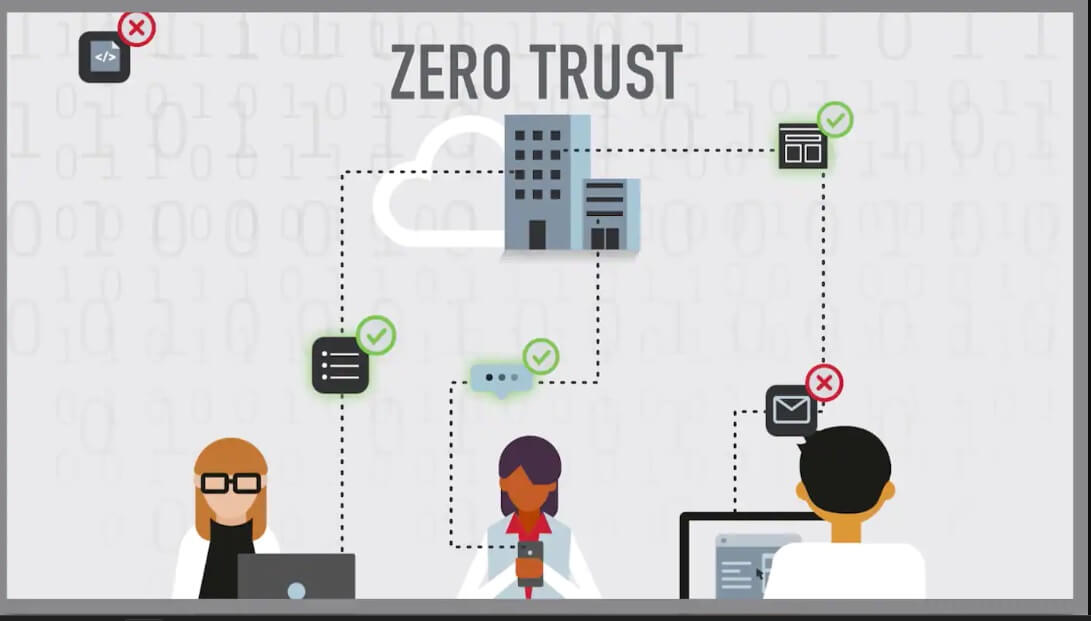
In the IT industry, the Zero Trust Model has gained significant popularity as a security framework. As its name says, this model operates under the idea that organizations should not automatically trust any user, device, or application, even if these are within the organization's network perimeter.
Instead, the traditional security model assumes that once a user or device is within the organization's network perimeter, it can automatically be trusted. But, with the increasing sophistication of data breaches and other cyber-attacks, this old model represents a real risk to your privacy.
If your company still operates under standard practices, it may be time to shift to the zero-trust model. The Zero Trust Model takes a different approach by requiring constant verification and authentication of all users, devices, and applications, regardless of the location.
However, implementing a Zero Trust Model requires significant planning, investment, and ongoing maintenance. Adopting the Zero Trust Model also requires modifications to technical solutions like multi-factor authentication and network segmentation, as well as the organization's culture and processes.
Moving forward...
As we've outlined, electronic devices can hold a surprising amount of information that could represent a real risk whenever it ends in the wrong hands, so please wipe out all your data before disposing of your excess equipment.
With years of experience in the ITAD industry, GreenTek Solutions offers an extensive range of secure data destruction services to protect all your confidential data. Contact us today!!